By utilizing Snapshots, you eliminate the need for manual setup for each account, significantly reducing setup time and minimizing the potential for errors. This streamlined approach not only accelerates the onboarding process but also enhances the overall user experience by providing immediate access to well-organized and meaningful data insights.
Loading a Snapshot into a Sub-Account
Navigate to Sub-Accounts
In the "Sub-Accounts" tab, search for an existing sub-account or create a new one.
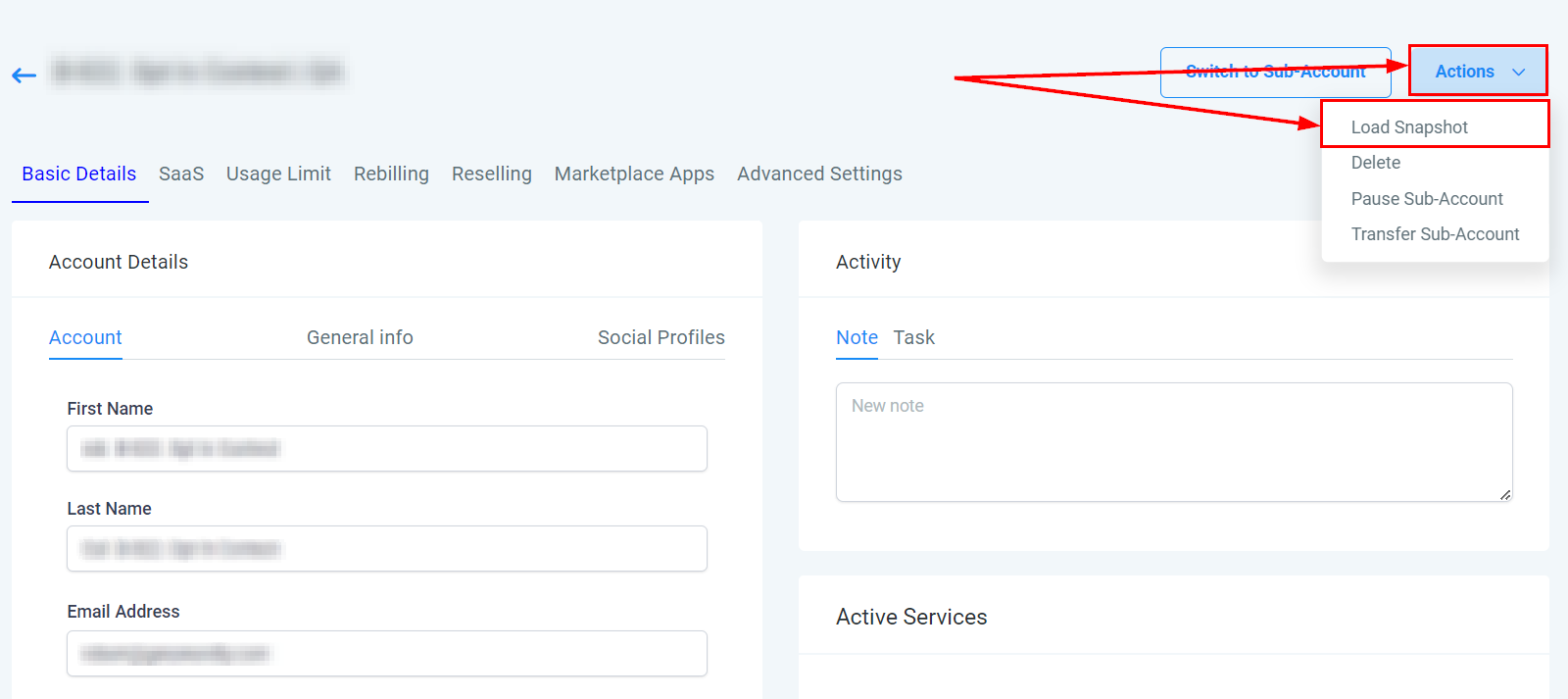
Load Snapshot
Select your sub-account and click "Load Snapshot" under the Actions dropdown.
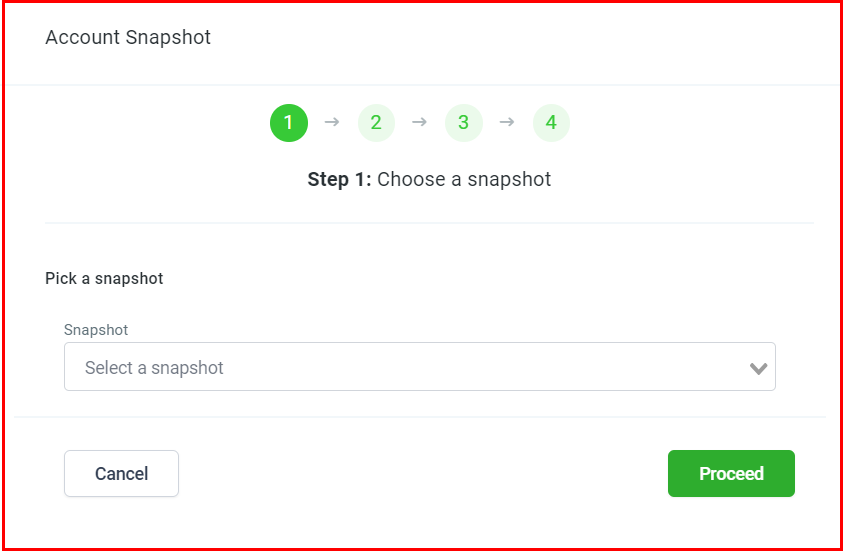
Select Desired Snapshot
Choose the snapshot to load and proceed.
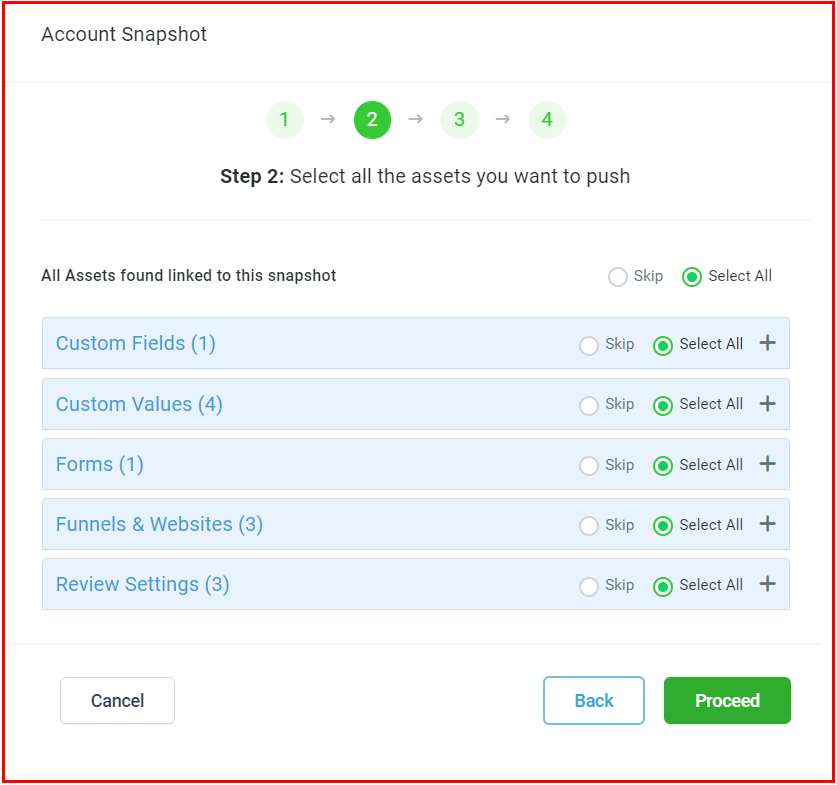
Select Assets
In the asset list associated with the snapshot, select the necessary assets to load into the sub-account. Click "Proceed."
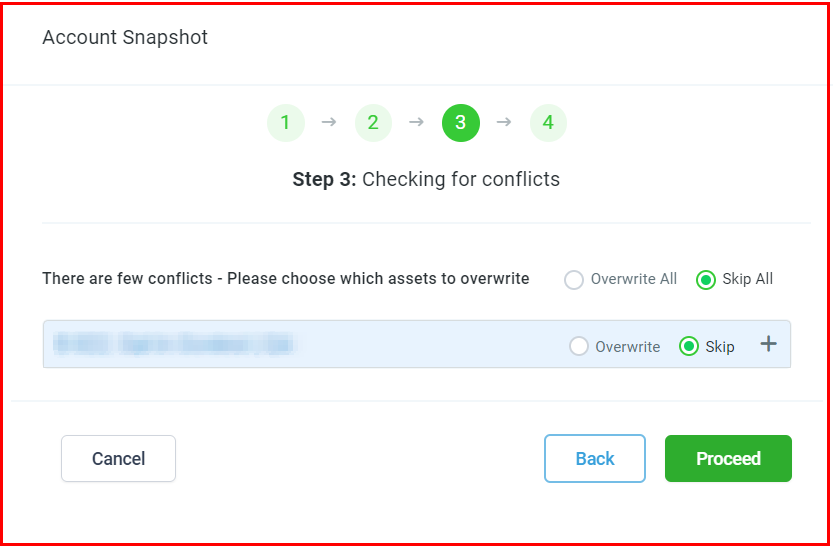
Checking for Conflicts
Any conflicts between the selected assets and existing assets will be displayed in this tab. You will have the option to either skip or overwrite the existing asset.
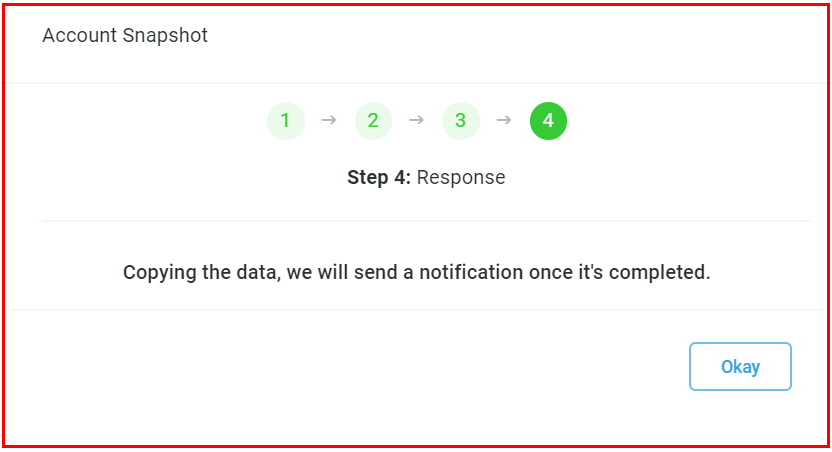
Completion Notification
The system will notify you when the snapshot upload is complete.
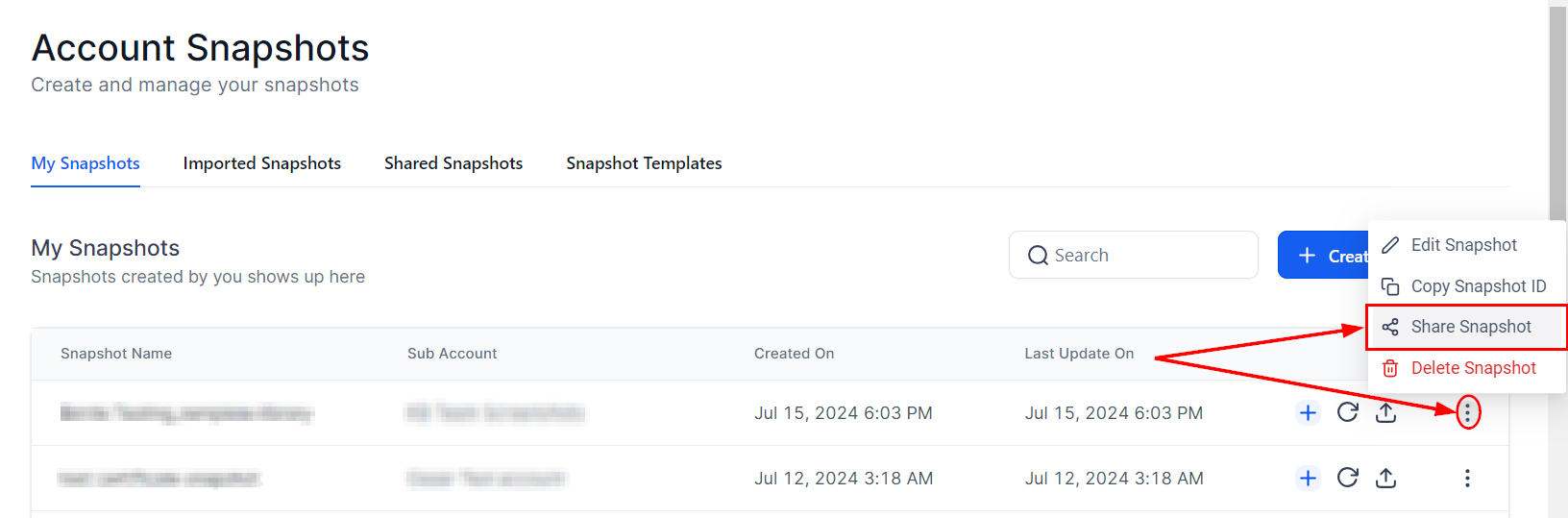
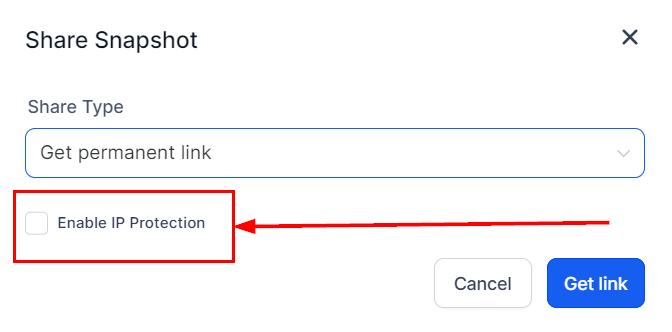
IP Protection in Snapshot Sharing
When sharing snapshots, you have the option to enable IP protection to prevent others from creating new snapshots from your shared assets. A modal facilitates the generation of a shared link with IP protection enabled. This modal provides a detailed view of all assets included in the snapshot, clearly indicating those that are restricted (IP protected) and, therefore, excluded from the snapshot.
Enabling IP Protection
While generating a snapshot share link, select the checkbox to enable IP protection.
Benefits
- Streamlined Onboarding: Pre-configured accounts using snapshots ensure a seamless and efficient onboarding process.
- Consistent User Experience: Easily replicate and deploy comprehensive assets across all locations, providing consistent and valuable insights.
- Enhanced Security: IP protection ensures your assets are secure and cannot be redistributed, preserving their value.
By following these steps and utilizing the enhanced IP protection features, you can efficiently manage and deploy snapshots while safeguarding your intellectual property.